- Domains
- DNS Management
- Content Delivery Network
-
Cloud Containers
- Overview
-
Using Containers
- Creating and Managing
- Connecting to a Container
- Swapping the Image
- Domain Aliases
- Environment Variables
- Protected Environment Variables
- Backing Up
- Automatic Updates
- SSL Support
- Adjusting Execution Time Limits
- Upgrading Apache Image
- Renaming a Container
- Port Management
- Caching
- Cloning/Overwriting
- Restoring a Backup
- Production Mode
- Metrics Dashboard
- Accessing supervisord
- Container Deprecation
- SSH / SFTP Users
- Databases
- Volumes
- Custom Images
-
Technical Guides
- Create a NodeJS Container
- Creating a Service Container
- Working with .NET Core Web Containers
- Working with Node.js Web Containers
- Working with Umbraco Web Containers
- Deploying your application with git
- Python Container
- Enable Country-Level blocking in Cloud Containers
- Working with SQL Server Containers
- Working with the SilverStripe Caching folder
- Profiling a site using Xdebug on Cloud Containers
- Working with SilverStripe Containers
- NGINX Proxy for Service Containers
- Tuning PHP OPcache
- Low Disk Warnings & Upgrades
- Local Development
- Virtual Servers
- Dedicated Servers
- Private Cloud
- Cloud / Shared Hosting
- Email Hosting
- Monitoring & Bandwidth
- Account & Billing
- Developers
- SSL Certificates
Server Firewalls
Firewalling features are available on our Standard Virtual Servers, or High Performance Virtual Servers on our newest virtualisation platform.
Attaching Security Groups
If you already use tools like
ufworiptableson your server, please read the Application Firewalling section before continuing.
Each server has a Firewall page which can be used to apply your Security Groups .
- When logged into the Control Panel , click Servers in the left menu.
- Select the server you want to configure, from the table on screen
- Click the tab at the top of screen labelled Firewall. If the tab is not visible, firewalling is unfortunately not available for your server.
- Select the Security Group(s) you wish to apply to your server, and click Save Firewall
Group Ordering
Similar to the way that firewall rules within Security Groups work, any groups you attach to your servers are applied in order from top to bottom.
- A given Security Group can only be used once per server
- A general
DROPrule at the bottom of one Security Group, will prevent rules in any subsequent groups from being reached
Application Firewalling
Security Groups run before any network traffic actually enters your server. This means that if your server is currently using application level rules such as ufw or iptables, you may need to disable or modify them to work with your groups:
- If you
ACCEPTa port/IP using Security Groups in the Control Panel, but your application firewall is blocking them, the traffic will still be blocked from reaching your server. - Similarly, if you
DROPa port or IP using Security Groups in the Control Panel, the traffic will never reach your server. This means that any application rules which would usually allow that traffic through, will never be reached.
Retained Access Groups
If you have server management enabled, or your server is a semi-managed product such as Cloud Containers, you may notice that there are some "greyed-out" Security Groups that are always present in your server's firewall. These are called "retained access" groups, and we use them to ensure we can access your server to perform administrative tasks related to your management.
We intentionally try to limit these groups to very specific traffic, to ensure they don't collide with any rules you may add. Some examples of the rules within these groups include:
- Retaining SSH access via certain IPs
- Allowing your server to push metrics (such as CPU usage) to our systems
Example
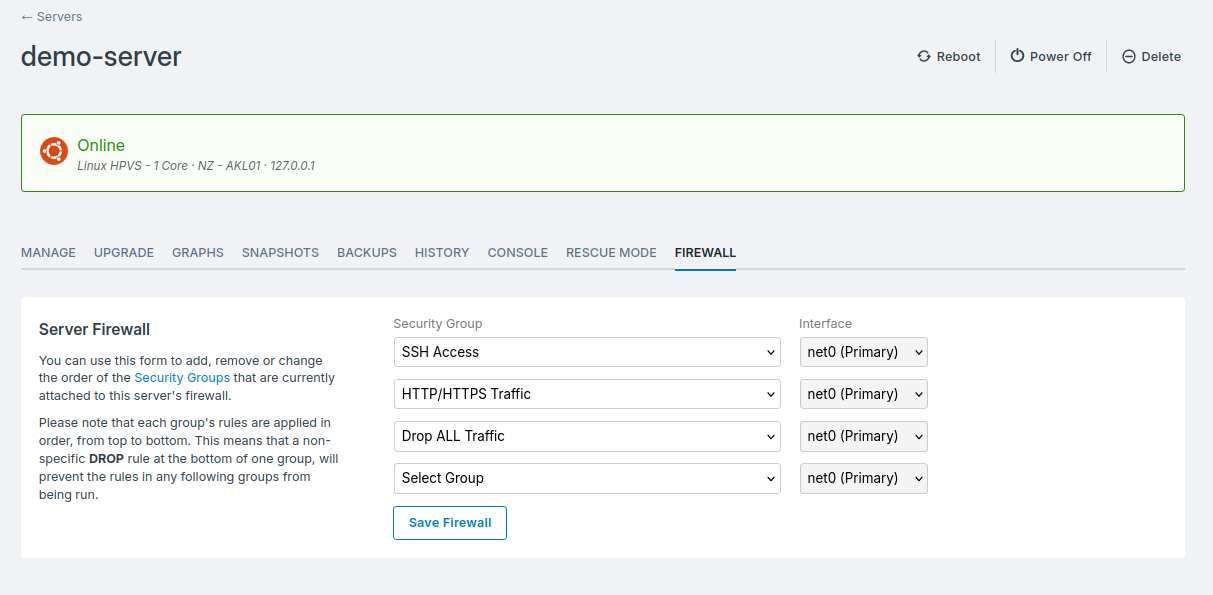
The image below shows an example configuration of a server firewall:
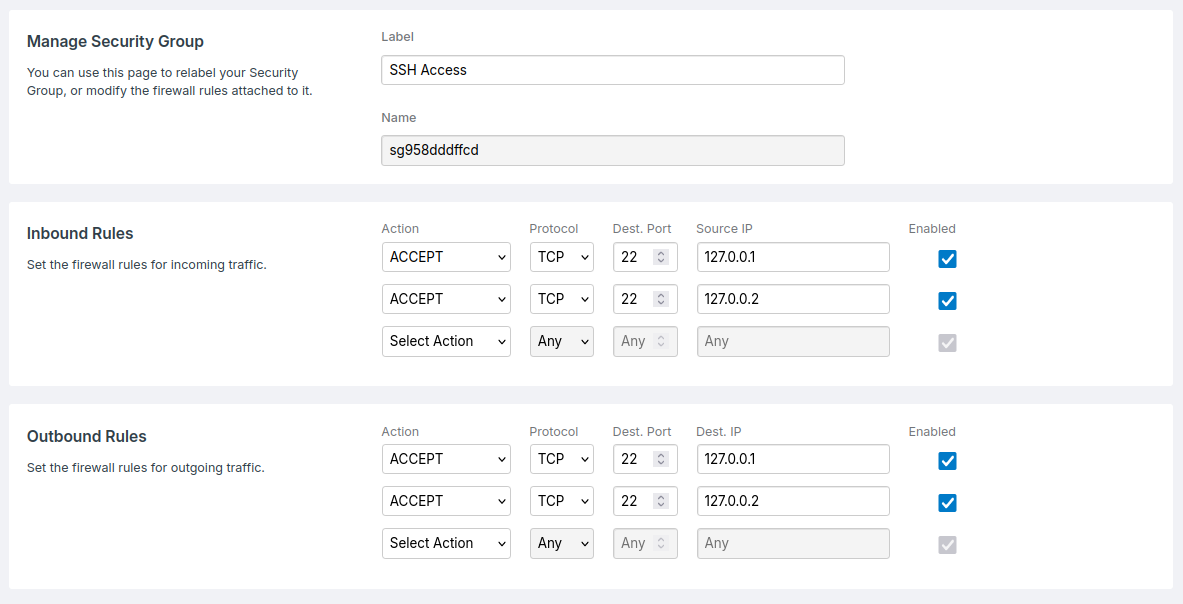
- The SSH Access group only contains
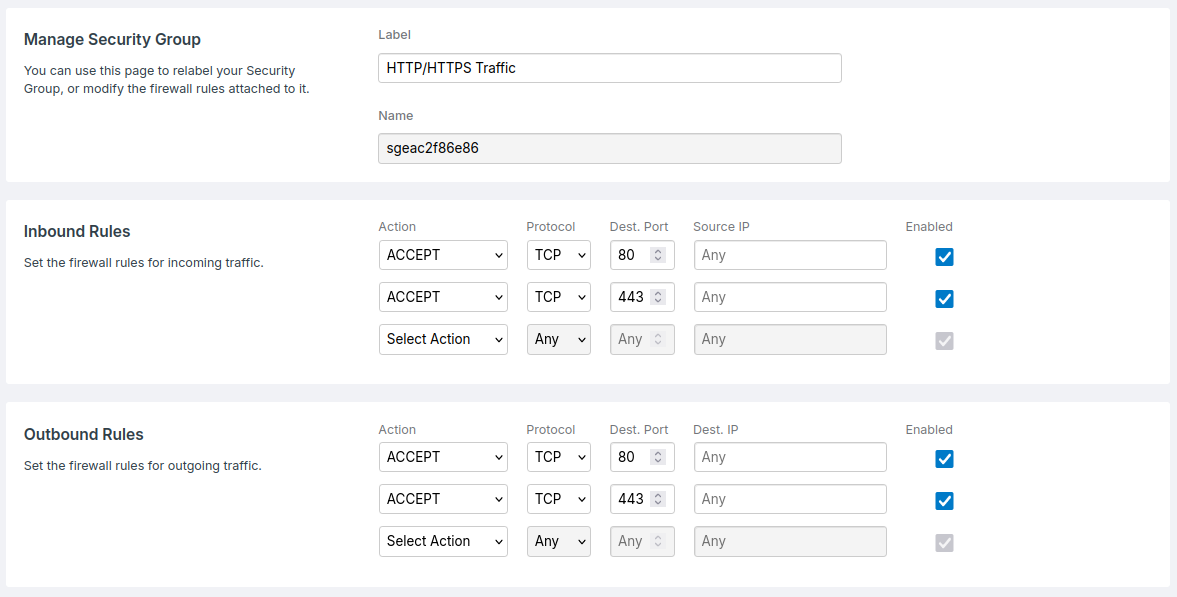
ACCEPTrules for port22, for the source IPs that should have access. - The HTTP/HTTPS Traffic group accepts all traffic related to ports
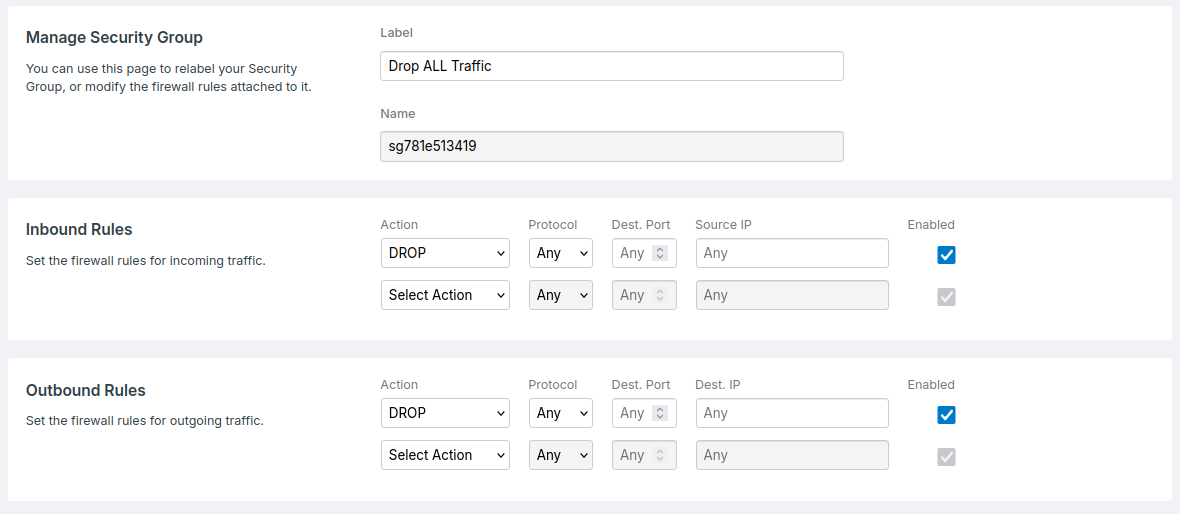
80and443, so that web traffic can interact with the server. - The Drop ALL Traffic group drops any remaining traffic, that has not been processed by group 1 and 2. Keeping the server secure from any other traffic.
Security Group Details
For completeness, the Security Groups in the above example could look like the following: