- Domains
- DNS Management
- Content Delivery Network
-
Cloud Containers
- Overview
-
Using Containers
- Creating and Managing
- Connecting to a Container
- Swapping the Image
- Domain Aliases
- Environment Variables
- Protected Environment Variables
- Backing Up
- Automatic Updates
- SSL Support
- Adjusting Execution Time Limits
- Upgrading Apache Image
- Renaming a Container
- Port Management
- Caching
- Cloning/Overwriting
- Restoring a Backup
- Production Mode
- Metrics Dashboard
- Accessing supervisord
- Container Deprecation
- SSH / SFTP Users
- Databases
- Volumes
- Custom Images
-
Technical Guides
- Create a NodeJS Container
- Creating a Service Container
- Working with .NET Core Web Containers
- Working with Node.js Web Containers
- Working with Umbraco Web Containers
- Deploying your application with git
- Python Container
- Enable Country-Level blocking in Cloud Containers
- Working with SQL Server Containers
- Working with the SilverStripe Caching folder
- Profiling a site using Xdebug on Cloud Containers
- Working with SilverStripe Containers
- NGINX Proxy for Service Containers
- Low Disk Warnings & Upgrades
- Local Development
- Virtual Servers
- Dedicated Servers
- Private Cloud
- Cloud / Shared Hosting
- Email Hosting
- Monitoring & Bandwidth
- Account & Billing
- Developers
- SSL Certificates
TLS Version
What is TLS?
TLS is short for Transport Layer Security. It is a cryptographic protocol that provides end-to-end communications security over networks and is widely used for internet communications and online transactions. You can read more information about TLS on the Transport Layer Security Wikipedia page.
Are we using TLS in our Cloud Container servers and what versions of TLS do Cloud Container servers support?
TLS is built-in to our Cloud Container platform. If a container is SSL enabled HTTPS connections will automatically use TLS v1.1, v1.2 or v1.3. You can decide which version of TLS your Cloud Container server uses via the Settings screen and it will apply to all containers on the server:
- When logged in to the SiteHost Control Panel, click the Servers module from the menu on the left.
- Click on the Cloud Container server that you would like to adjust TLS for.
- Now click on the Settings tab and you will see the TLS option, select your preferred option and then Save Changes.
- Your change will be applied in a few seconds and the selected version of TLS will be used.
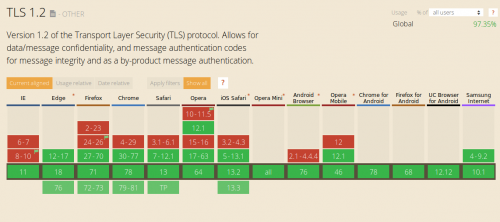
Why should you use TLS v1.2 and above?
Many improvements have been made since the release of these versions and upgrading to the current standard (TLS 1.2 and TLS 1.3) is now considered the safest and most reliable method of delivering encrypted content over the Internet.
What are the pros and cons of using TLS v1.2 and above?
Where are SSLv3 and TLS v1.0?
SSL is the predecessor of TLS. As with any software development or protocols, it becomes less secure and phased out as technology advanced. TLS v1.0 was based heavily on SSL and designed to solve compatibility issues therefore, it suffers the same vulnerabilities as SSL. As such, back on June 30, 2018, websites will need to stop supporting TLS 1.0, SSLv3 and earlier to remain PCI compliant.
How about TLS v1.1?
TLS v1.1 is fairly dated versions of the TLS protocol. It was published in 2006 as RFC 4346. Although improvements have been made in TLS v1.1, researchers found that it is still vulnerable to similar attacks as TLS v1.0.